Peter Lobner
George Orwell’s novel Nineteen Eighty-Four was published 70 years ago, on 8 June 1949. Together with his political allegory Animal Farm published in 1945, Nineteen Eighty-Four brought Orwell worldwide fame. As I hope you know, Nineteen Eighty-Four describes a dystopian future occurring in 1984 (now 35 years in our past) in which a totalitarian government imposes repressive regimentation on all persons and behaviors through prescriptive laws, propaganda, manipulation of history, and omnipresent surveillance. Fortunately for us, the real year 1984 fared much better. However, Orwell’s vision of the future, as expressed in this novel, still may be a timely and cautionary tale of a future yet to come.

Source: Wikipedia

You’ll find an interesting collection of quotations attributed to George Orwell on the AZ Quotes website here:
https://www.azquotes.com/author/11147-George_Orwell
You can read Nineteen Eighty-Four chapter-by-chapter online on The Complete Works of George Orwell website at the following link, which also contains other Orwell novels.
https://www.george-orwell.org/1984
You also can read Nineteen Eighty-Four as one file on the Project Gutenberg Australia website at the following link:
http://gutenberg.net.au/ebooks01/0100021.txt
Here, it’s easy to search the whole novel for key words and phrases, like “Though Police,” “Big Brother,” “Ministry of Truth,” “thoughtcrime,” “crimethink,” and “face crime,” and see how they are used in context.
Orwell was right about the concept that an entire population can be kept under constant surveillance. However, he probably didn’t appreciate the commercial value of such surveillance and that people voluntarily would surrender so much information into an insecure (online) environment, thereby making it easy for agents to legally or illicitly collect and process the information they want. Today, it’s hard to know if Big Brother is the government or anonymous aggregations of commercial firms seeking to derive value from your data and influence your behavior.
With the increasing polarization in our society today, it seems to me that we are entering more precarious times, where our own poorly defined terms, such as “politically correct” and “hate speech,” are becoming tools to stifle alternative views and legitimate dissent.
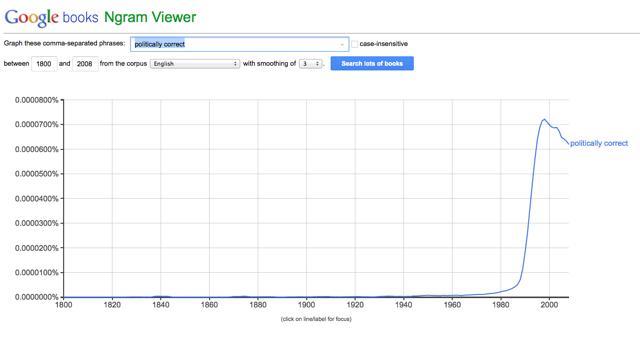
I remember in the late 1970s when I first read the words “politically correct” in Jim Holman’s local San Diego newspaper, Reader. My first reaction to this poorly defined term was that it will lead to no good. Since then, use of “politically correct” has grown dramatically, as shown in the following Google Ngram. While I agree that political correctness has its place in a polite society, the muddled jargon of political correctness easily can becomes a means to obfuscate a subject under discussion.
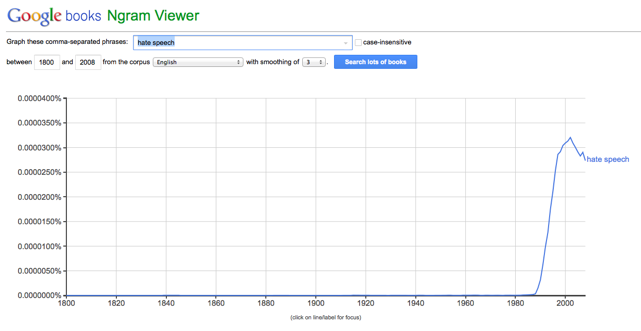
In the past two decades, use of the term “hate speech” has become commonplace, as shown in the following Google Ngram. While laws have been written to define and combat actual “hate speech,” this term is easily misused to stifle dissent, even legitimate dissent, by forcefully mischaracterizing one side of a discussion that never was intended to be hateful. Our ability to hold opposing views without being mischaracterized as a “hater” is being eroded in our increasingly polarized society, where self-appointed (and often anonymous) Thought Police are using social media (What an oxymoron!) to punish the perceived offenders. Such “policing” is not centralized, as in Orwell’s novel, but its effects can be very damaging to its victims.
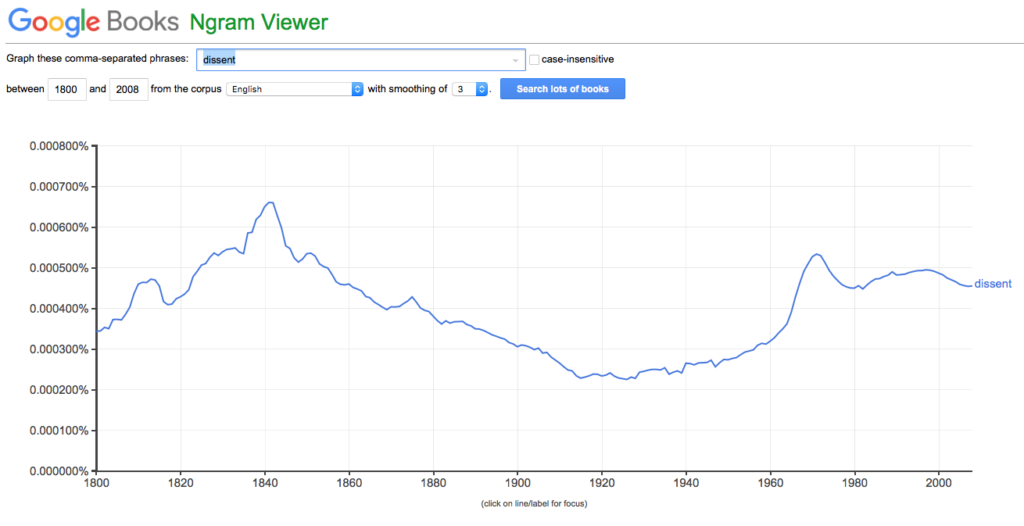
Of course, the word “dissent” has been in common usage for a very long time and is a fundamental right of American citizens.
Seventy years after first being published, Orwell’s novel Nineteen Eighty-Four still stands as a relevant cautionary tale for our own future. I encourage you to read it again, keep an open mind, and piss off the self-declared Thought Police from time to time.